The unseen battle: Why you need secure coding now more than ever
Data breaches, financial losses, and public scandals—they’re all over the news. And behind each story is a question few people think to ask: Why do these breaches keep happening? For companies focused on innovation, secure coding is often the first line of defence against malicious actors. Yet, it’s too often sidelined in the rush to roll out new features.In this article, we’ll explore why secure coding should be a non-negotiable part of your development strategy. You’ll learn about the common coding vulnerabilities attackers exploit, and discover simple, actionable steps to protect your code—and your business.
The cost of prioritising features over security
With competition growing, businesses face constant pressure to innovate. New features create excitement and drive revenue, but every added feature is also a new entry point for attackers. That’s where secure coding comes in—an invisible but essential foundation.
The truth is many organisations still see security as an optional add-on rather than a core part of the development process. But as Jack Misiura, Application Security Manager at The Missing Link, put it, “Secure coding isn’t a feature; it’s a necessity.” Without it, you’re building on shaky ground.
The real-world impact of this can be devastating. Recent high-profile breaches have rocked major companies like Twitter, Ticketmaster, Optus, and Medibank. Even organisations with advanced resources fall victim to preventable vulnerabilities, like SQL injections and cross-site scripting (XSS) attacks. By embracing secure coding, you can avoid becoming the next headline.

The democratisation of hacking and the growing risk you face
Here’s the frightening reality: hacking is no longer just for organised criminal groups. Today, even teenagers with access to online tutorials can carry out sophisticated attacks.
This “democratisation of hacking” has lowered the barrier for cybercriminals, making businesses of every size potential targets. A quick Google search on “how to hack a server” brings up endless tutorials and tools, turning novices into potential threats.
So, why hasn’t secure coding caught up? Despite excellent resources like the OWASP (Open Web Application Security Project) framework, secure coding practices still lag because many developers haven’t been trained to adopt these methods.
This imbalance—an abundance of hacking resources and a shortage of secure coding training—leaves your organisation vulnerable.
Understanding common coding vulnerabilities you're up against
During our recent webinar, we showcased a simulated application to highlight some of the most common vulnerabilities developers encounter:
- Cross-site scripting (XSS): Attackers use XSS to inject malicious scripts into web pages, gaining unauthorised data access.
- SQL injection: By tampering with SQL queries, attackers can break into databases and steal sensitive information. In our demo, this was how attackers fraudulently authorised massive payouts.
- Broken object level authorisation (BOLA): Weak authorisation controls allow attackers to access restricted areas, escalate privileges, or leak sensitive data.
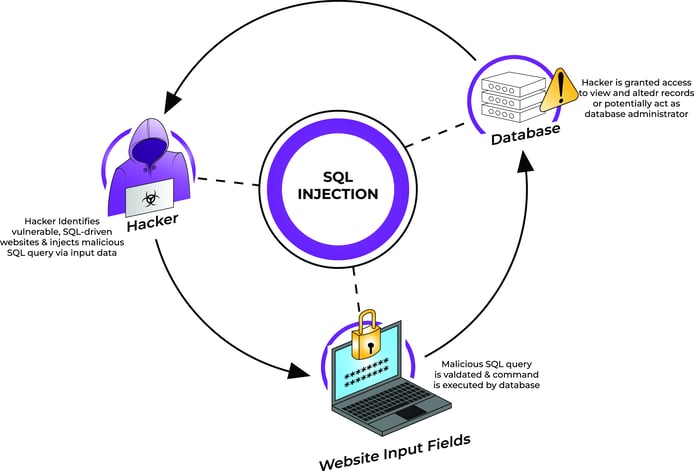
In our demo, a single XSS vulnerability gave attackers initial access. By chaining vulnerabilities like SQL injection, they escalated their privileges, leading to full system compromise. Hackers don’t need just one open door—they create a path by stringing together multiple minor vulnerabilities. This shows why even small flaws in your code need attention.
The hidden dangers of discount codes
Discount codes might seem harmless, but they’re a common entry point for attackers. Here’s how it works: hackers create a convincing fake website offering an exclusive deal, asking users to enter their details for a “valid” discount code.
Once users enter their information, attackers have everything they need to launch phishing attacks, steal identities, and even commit financial fraud.
In our demo, we showed how a discount code field could become a gateway for attack. A cross-site scripting (XSS) vulnerability allowed hackers to inject malicious code, transforming an innocent-looking input box into a powerful tool for data theft.
For developers, securing every input field is essential. Remember to validate, encode, and secure all user input, especially in places like discount or promotional fields. As a user, only trust discount codes from verified sources. A harmless-looking discount might cost more than you think.
3 essential pillars of secure coding
To safeguard your systems, consider these three essential strategies for integrating secure coding practices into your development lifecycle:

-
-
1. Prioritise input validation
Input validation is one of the most effective defences against attacks. By controlling the data that enters your systems, you limit opportunities for hackers. - Make sure to implement server-side validation rather than relying on front-end UI, as attackers can bypass front-end controls easily. This includes ensuring that third-party libraries aren’t fed direct user input without thorough validation.
-
-
2. Employ layered security testing tools
Security tools are essential to uncover vulnerabilities. Implement multiple layers: Static Application Security Testing (SAST) scans your code for vulnerabilities, while Dynamic Application Security Testing (DAST) checks for weaknesses in your running application. - Add Software Composition Analysis (SCA) to identify risks in third-party libraries, ensuring you’re covered across every entry point. However, remember that tools alone are not a silver bullet—they should work alongside manual testing and secure coding practices.
-
-
3. Invest in developer training and engagement
Secure coding practices need to be second nature to every developer, not just security teams. Regular, hands-on training can help developers understand the mindset of attackers and write more resilient code. - To keep training engaging, consider gamified sessions that simulate real-world attacks so your team can see secure coding in action. Make sure developers understand not only how to code securely but also why security is so crucial. Only when they grasp the stakes will security become a habit rather than an afterthought.
-
Avoiding common coding mistakes
Even with the best intentions, developers can introduce vulnerabilities by taking shortcuts under pressure. Here are some common mistakes to watch out for:
| Sanitising user input | Instead of trying to “clean up” what users enter, focus on encoding it to prevent malicious characters from being interpreted as code. |
| Unparameterised SQL queries | Always use parameterised queries to prevent SQL injection attacks, especially when dealing with databases. |
| Assuming front-end validation is enough | Front-end controls are for user experience, not security. Make sure all validation happens server-side to protect against malicious actors bypassing UI restrictions. |
Securing third-party code
Third-party code often becomes a gateway for attacks. You likely use libraries and frameworks to speed up development, but each one introduces a potential vulnerability. To protect your code:
| Validate inputs | Third-party code should never be given direct user inputs without validation. |
| Limit input length | Control the data size to prevent buffer overflow attacks. |
| Monitor for updates | Regularly check for security patches and updates from your third-party providers. |
Unit testing for security to keep bugs out of your code
Security-focused unit testing can help prevent vulnerabilities from reappearing as your code evolves. Security unit tests, unlike traditional tests, should check for both the “happy path” (confirming the vulnerability is absent) and the “unhappy path” (confirming that attempts to exploit vulnerabilities fail). This ensures that you catch issues before they reach production.
Empowering your development team with secure coding
Secure coding might seem daunting, but every step you take improves protection for your users, your reputation, and your business’s future.
Cybercriminals aren’t going away, but by prioritising secure coding, your development team becomes the first line of defence. In the world of cyber security, it’s not a question of if you’ll be targeted—it’s a matter of when.
Ready to dive deeper? If you want a closer look at how attackers exploit common coding vulnerabilities and the steps you can take to secure your applications, check out our on-demand webinar.
You’ll gain practical insights into secure coding techniques, see real-world demonstrations, and get expert advice from Jack Misiura on fortifying your code against evolving threats.
Author
As a Content Marketing Specialist at The Missing Link, I turn technical insights into engaging stories that help businesses navigate the world of IT, cybersecurity, and automation. With a strong background in content strategy and digital marketing, I specialise in making complex topics accessible, relevant, and valuable to our audience. My passion for storytelling is driven by a belief that great content connects, educates, and inspires. When I’m not crafting compelling narratives, I’m exploring new cultures, diving into literature, or seeking out the next great culinary experience.
- The cost of prioritising features over security
- The democratisation of hacking and the growing risk you face
- Understanding common coding vulnerabilities you're up against
- The hidden dangers of discount codes
- 3 essential pillars of secure coding
- Avoiding common coding mistakes
- Securing third-party code
- Unit testing for security to keep bugs out of your code

