Cyber Security.
7.07.16
Over the first half of 2016 there has been a rise of phishing emails doing the rounds. The latest appear to be from the Australian Federal Police (AFP), Australia Post, AGL and Telstra. The emails are good imitations of legitimate emails you may receive from these companies and people should be on the look out for them. Unlike ‘traditional’ phishing emails that may try and steal your personal information for future use, these emails are carrying malware. Some of these emails are such good imitations it’s hard to recognise that they’re not legitimate.
The Australian Government SCAMwatch websitedescribes phishing scams as “attempts to trick you into giving out personal information such as your bank account numbers, passwords and credit card numbers.”
A phishing scam comes out of the blue via email, phone call, text message or social media. The scams are disguised as being from a legitimate business such as a shipping company or bank and you are asked to provide or confirm your personal details. In writing via email, text or social media you are asked to click on a link to confirm your personal details before your account is suspended(for example), via phone you may be asked survey questions and offered a prize for participating.
Whaling and spear-phishing scams target businesses to get confidential information. Pharming takes you to a fake version of a legitimate website – after infecting your computer with malware you will be redirected to the fake site even if you type the genuine address in your browser or click on a previously bookmarked link.
The current wave of emails are carrying Ransomware. Ransomware files encrypt files on the device that was used to open the fraudulent link or initiate a download from the email. In some cases it may encrypt the entire network, not just the single device. The user or business is then held to ransom, ransom payment is often demanded in Bitcoin. Many companies feel they are left with no choice but to pay the ransom to access the files however, after the ransom is paid the attackers usually demand a higher ransom and don't unlock the files. In the end, restoring from backup is usually the inevitable solution so businesses need to ensure they have robust backup systems and a Disaster Recovery Plan in place. The recent spate of emails have been infected with Torrentlocker and Cryptolocker.
Phishing messages look genuine at first glance, using the logo and other branding elements of the company they are imitating, they may even have a similar website address. Below is an example of a phishing email, as you can see it has many elements which make it seem suspicious. Keep in mind some phishing emails look a lot more legitimate than this one and may only have one or two suspicious elements:
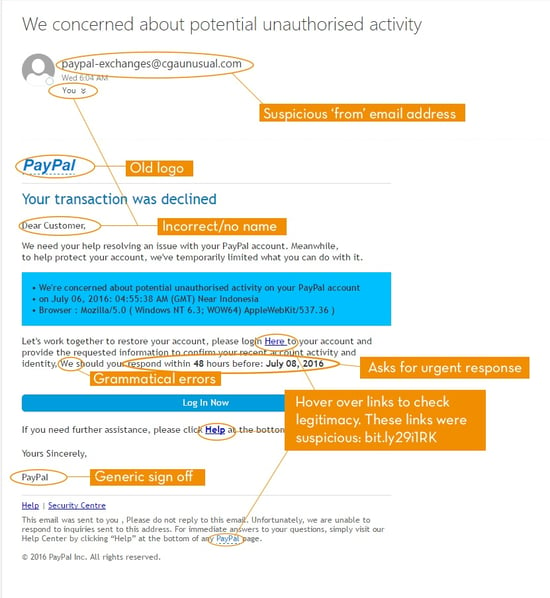
> Generic/no or incorrect name used in the salutation, eg Dear “Customer”
> Spelling and/or grammatical errors
> Suspicious looking sender email address
> A sense of urgency “respond immediately or your account will be suspended”
> Check link addresses by hovering over them (don’t click on them!)
> You have no association with the company sending the email
> You are a regular company of the customer but this email is different from the ones you usually receive
Never click on any links in these emails. You should send the email to your IT Department, and you can mark or report it as junk or a phishing scam (different email applications have different protocols for reporting these types of emails). All scam emails received in Australia can be reported to the ACCC via the SCAMwatch Website.
You can also report the scam directly to the company that is being imitated. Most companies have a dedicated email address to send these types of emails too, for example: phishing@paypal.com.au.
> Subscribe to the Stay Smart Onlinefor the latest news.
> Put updates on your company Intranet alerting staff to current emails.
> Educate staff on what to look out for and regularly test staff.
> Contact our award-winning Security team for a security audit.
If you liked this article you may also like:
How can I create an unbreakable password?
The 6 worst apps that violate your privacy
Breach preparedness, no organisation is immune from a breach
Author